

Installation and Set-Up > Setting Data Storage Location Security > Standard File System Recommended Security Settings
 
|
Standard File System Recommended Security Settings
In order to secure the file server storage location, we suggest the settings shown below, which provide the following behavior:
- Files can be created by authorized users, but not modified or deleted.
- Folders can be renamed, whether there are files in them or not (we allow this because when Windows Explorer creates a new folder, it always calls it "New Folder" and it, therefore, must be renamed). If you wish to prevent renaming of folders (and forgo the ability to rename New Folders), you can remove the "Delete" right for "This folder and subfolders" for the Users group and the OWNER RIGHTS group (if applicable) in the suggested settings below.
- Folders cannot be deleted if they have files in them.
- The owner or creator of a file cannot change its security permissions.
In addition to these file security settings, you may also wish to turn on Windows auditing functions for the data storage folder on the file server using the standard procedure.a. Disable Modifying or Deleting of Files by Users
1. Remove "CREATOR OWNER" rights on the folder, if present.2. Select the Advanced button on the Security tab of storage folder's Properties dialog and then select "Show advanced permissions".3. Use the folder configuration as shown:
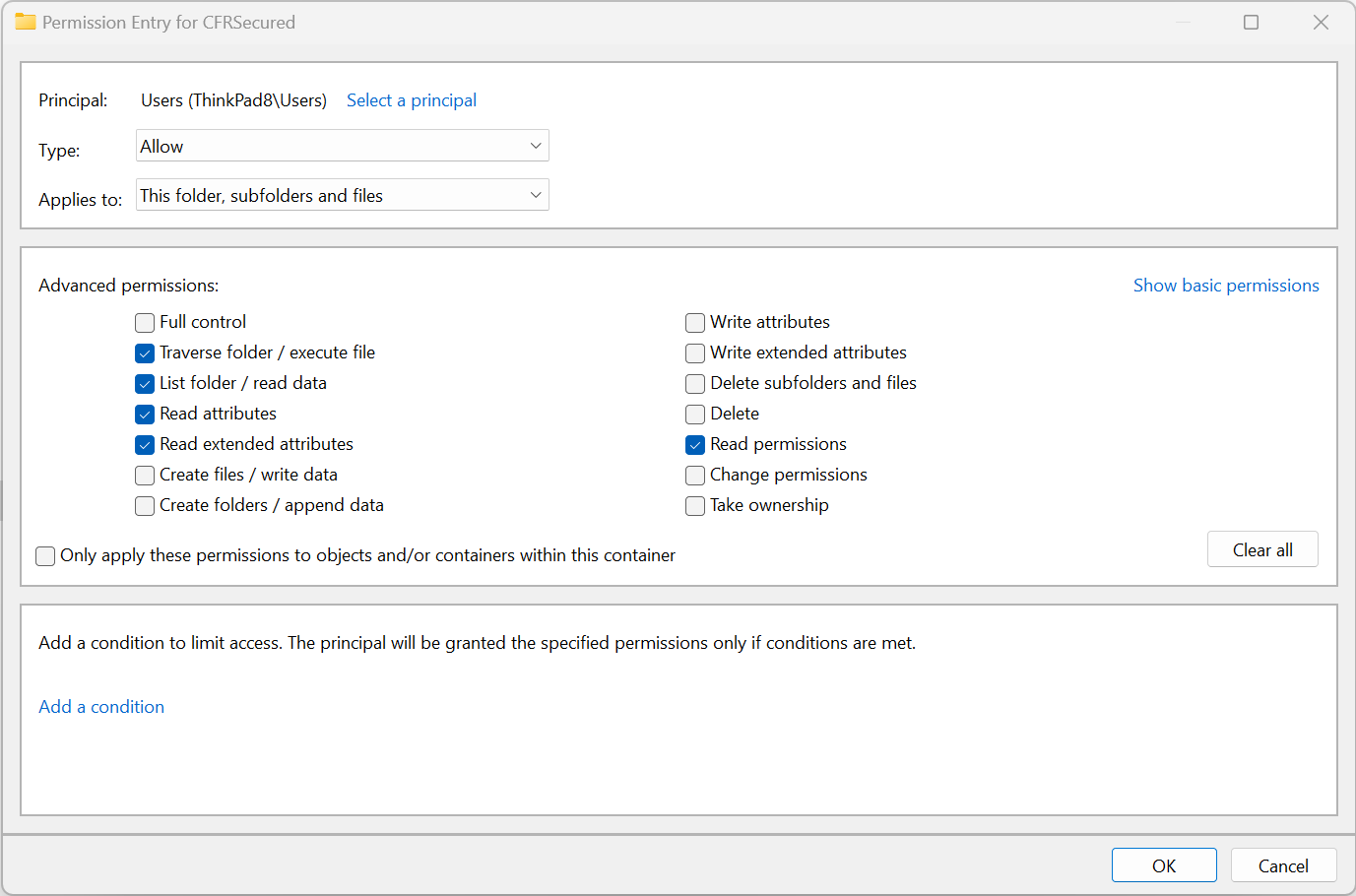
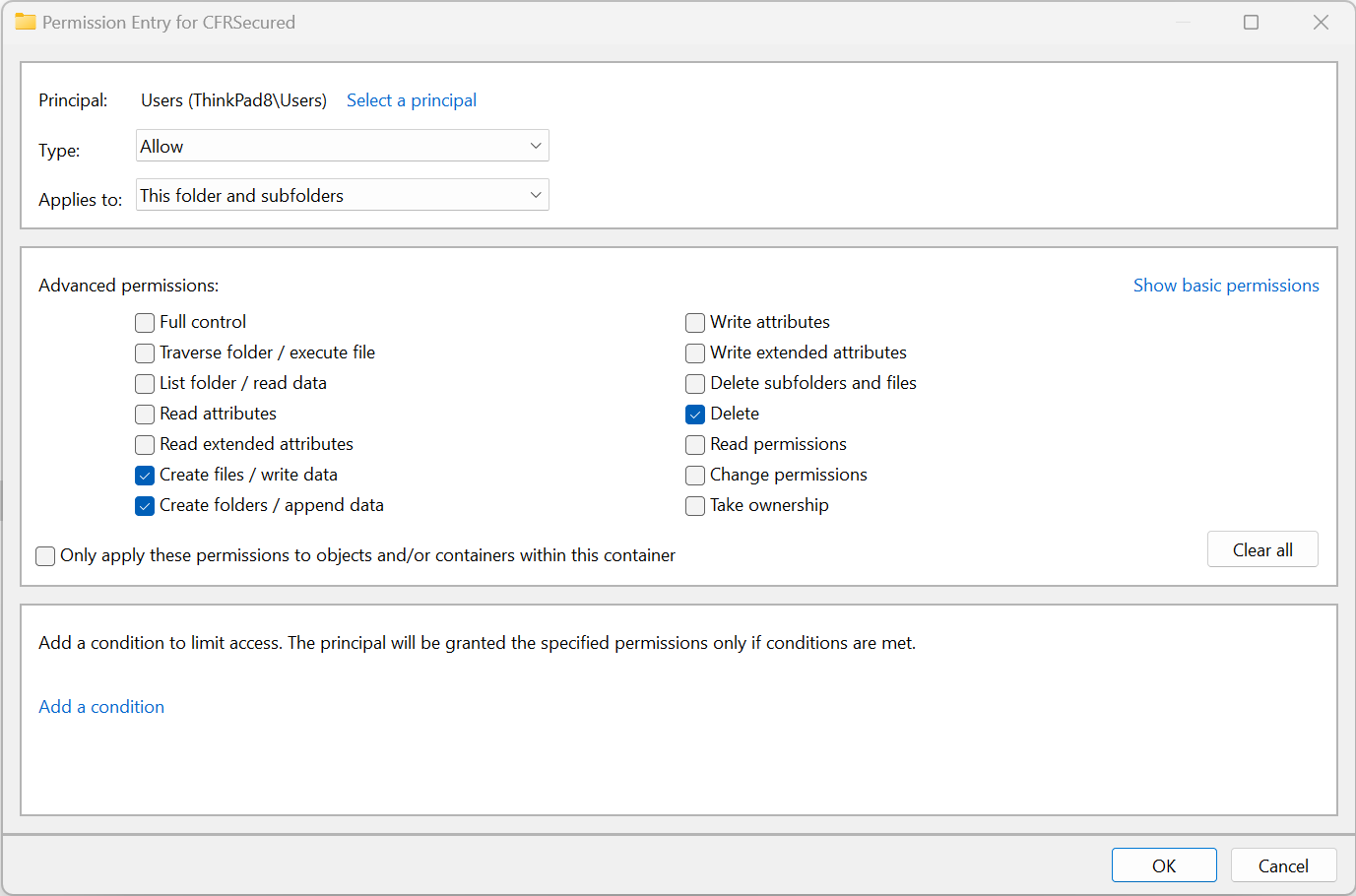
b. Disable Modifying or Deleting Files by Owner
1. Remove "CREATOR OWNER" rights on the folder, if present. Note that even if CREATOR OWNER is removed, the user that creates a file (the Owner) gets special rights to the file unless an "Owner Rights" security is specified as described below under Option 2.2. Prevent Owner from changing security settings on files:You can use the "OWNER RIGHTS" security principal to limit the rights for the file owner to delete the file or change it. For example, OWNER RIGHTS can be set to the same permissions as Users, as shown below.
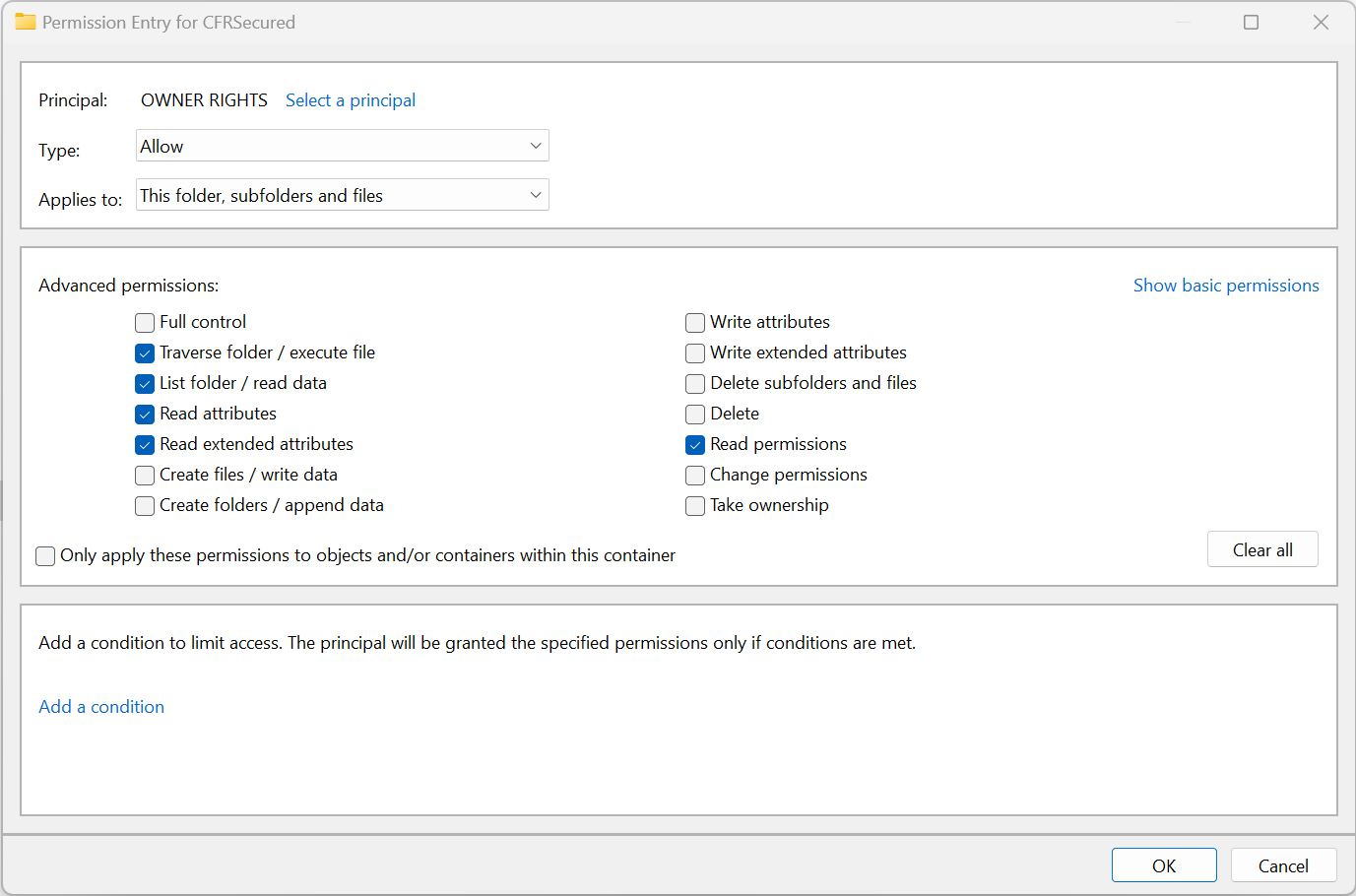

c. Restrict Administrator Access
If desired, you can remove or restrict access to files by Administrators of the file server by removing the Administrators group from the security settings for the folder. Note, however, that Administrators of the file server can still take ownership of a file because they automatically have the "Take Ownership" permission. When an Administrator of the server uses Take Ownership, the OWNER RIGHTS configuration is disabled. Then the new owner has the ability to modify the security of the file. Removing access by Administrators may help to prevent accidental deletion by Administrators, because such an operation would require three steps (take ownership, change permissions, delete file).
After completing these operations, the security settings for the storage location will be as shown below.
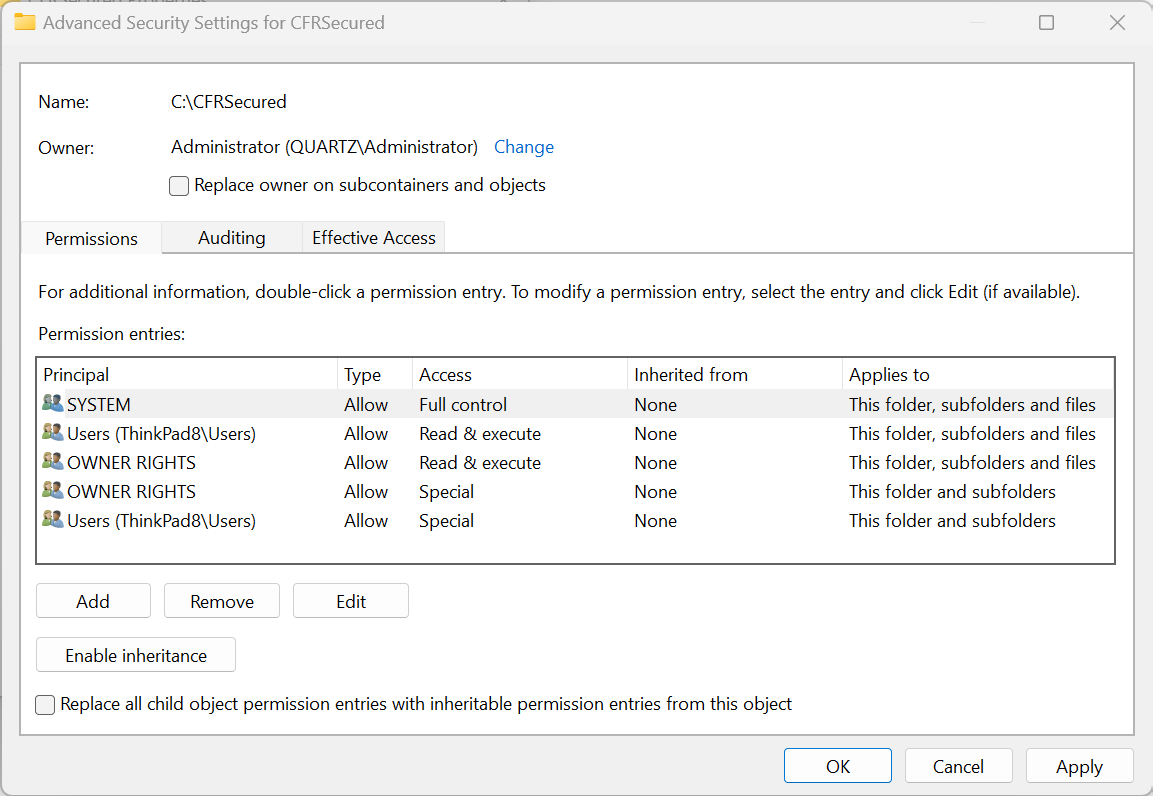
 
|